In the world of Virtual Private Networks (VPNs), the protocol you choose can significantly impact your online security, speed, and overall experience. VPN protocols dictate how your data is transmitted over the internet, influencing everything from encryption to connection stability. In this article, we’ll break down the most common VPN protocols—OpenVPN, L2TP, IKEv2, and others—so you can make an informed choice for your online needs.
What Are VPN Protocols?
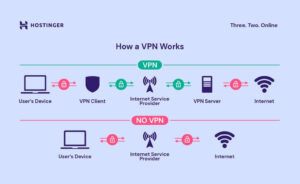
VPN protocols are sets of rules that determine how data is transmitted between your device and the VPN server. Each protocol has its own strengths and weaknesses in terms of security, speed, and ease of use. Understanding these differences is crucial for selecting the right VPN service for your specific requirements.

1. OpenVPN
Overview
OpenVPN is one of the most popular and versatile VPN protocols available today. It is open-source, which means its code is publicly available for scrutiny and improvement.
Strengths
- High Security: Uses AES-256 encryption, making it extremely secure.
- Customizable: Offers a range of configuration options, allowing users to tailor it to their needs.
- Cross-Platform Support: Compatible with various operating systems, including Windows, macOS, Linux, Android, and iOS.
Weaknesses
- Complex Setup: May require some technical knowledge to configure properly.
- Speed Variability: Performance can vary depending on server load and distance.
2. L2TP/IPsec (Layer 2 Tunneling Protocol)
Overview
L2TP is often paired with IPsec for encryption, providing a secure connection. This combination is commonly used in corporate environments.
Strengths
- Good Security: Offers strong encryption through IPsec.
- Widely Supported: Natively supported by most operating systems, making it easy to set up.
Weaknesses
- Speed Issues: Typically slower than other protocols due to double encapsulation (L2TP and IPsec).
- Firewall Issues: May face issues with firewalls and NAT (Network Address Translation) due to the use of multiple ports.
3. IKEv2/IPsec (Internet Key Exchange version 2)
Overview
IKEv2 is a tunneling protocol that is often combined with IPsec for encryption. It is known for its speed and stability, especially on mobile devices.
Strengths
- Fast Connection: Offers quick reconnection times, making it ideal for mobile users who switch networks frequently.
- Strong Security: Provides robust encryption through IPsec.
- Stability: Maintains a stable connection, even when switching between Wi-Fi and mobile data.
Weaknesses
- Limited Compatibility: Not as widely supported on all platforms as OpenVPN.
- Less Flexible: Fewer configuration options compared to OpenVPN.

4. PPTP (Point-to-Point Tunneling Protocol)
Overview
PPTP is one of the oldest VPN protocols and was developed by Microsoft. While it is fast and easy to set up, its security features are outdated.
Strengths
- Easy Setup: Simple to configure, making it user-friendly.
- High Speed: Offers fast connection speeds due to minimal encryption.
Weaknesses
- Low Security: Vulnerable to various security threats, making it unsuitable for sensitive data.
- Limited Encryption: Uses weak encryption methods, which can be easily compromised.
5. SSTP (Secure Socket Tunneling Protocol)
Overview
SSTP is a Microsoft-developed VPN protocol that uses SSL/TLS for encryption. It is particularly effective for bypassing firewalls.
Strengths
- Strong Security: Provides robust encryption through SSL/TLS.
- Firewall Bypass: Can easily navigate through firewalls and NAT.
Weaknesses
- Windows-Centric: Primarily designed for Windows, limiting compatibility with other platforms.
- Limited Open Source Options: Not as customizable as OpenVPN.
Choosing the Right VPN Protocol
When selecting a VPN protocol, consider the following factors:
- Security Needs: If security is your top priority, opt for protocols like OpenVPN or IKEv2/IPsec.
- Speed Requirements: For high-speed connections, IKEv2/IPsec or OpenVPN (with the right settings) are preferable.
- Ease of Use: If you want a straightforward setup, L2TP/IPsec or PPTP may be more suitable.
- Compatibility: Ensure the protocol you choose is compatible with your devices and operating systems.
Conclusion
Understanding VPN protocols is essential for making informed decisions about your online security and privacy. Each protocol has its unique features, strengths, and weaknesses. By evaluating your specific needs—whether it’s security, speed, or ease of use—you can choose the right VPN protocol for your digital lifestyle.
Call to Action
Ready to enhance your online security? Explore our top VPN recommendations HERE that support various protocols, ensuring you find the perfect fit for your needs. Protect your privacy today and enjoy a safer internet experience!


Great beat ! I would like to apprentice while you amend your web site, http://www.hairstylesvip.com how could i subscribe for a blog site? The account helped me a acceptable deal. I had been a little bit acquainted of this your broadcast provided bright clear concept
Good web site! I truly love how it is easy on my eyes and the data are well written. http://www.hairstylesvip.com I am wondering how I could be notified whenever a new post has been made. I’ve subscribed to your RSS which must do the trick! Have a nice day!
Thanks for posting. I really enjoyed reading it, especially because it addressed my problem. http://www.hairstylesvip.com It helped me a lot and I hope it will help others too.